Good To Know Before Reading:
Democratic People’s Republic of Korea (DPRK; North Korea)
STEM: science, technology, engineering, and math education
TTP: Tactics, Techniques, Procedures
Echo Chamber Effect (Media): An environment in which a person encounters only beliefs or opinions that coincide with their own, so that their existing views are reinforced and alternative ideas are not considered.
Wiper: In computer security, a wiper is a class of malware intended to erase the hard drive or other static memory of the computer it infects, deleting data and programs.
Shamoon: Also known as W32.DistTrack, is a modular computer virus that was discovered in 2012.
Doxxing: Publishing someone’s information online without their permission. (In crypto it means a person or entity who has identifiable information about themselves made public on the internet.)
Cover source: A woman ripping an American flag is depicted in a North Korean propaganda poster with a headband marked ‘US military out!’ Its main heading: ‘Repel the American invader.’

- Entities in the Republic of Korea and the United States: North Korea’s 2 longtime geopolitical adversaries – the victims of the majority of cyberattacks attributed to threat actors sponsored by the North Korea.
- North Korean threat actors maintain a global reach as well, targeting entities in at least 29 different countries since 2009.
- The targets and purpose of cyberattacks vary between threat actors — for instance, Kimsuky-attributed attacks have targeted entities in South Korea for espionage purposes, while Lazarus Group appears to have a much more diverse scope and global purview, targeting entities in a multitude of countries for various reasons.
- North Korea has been linked to an ever-increasing number of cryptocurrency heists, but the regime’s primary goal in its use of cyberattacks continues to be espionage.
Key Findings
- The primary objective of North Korea’s cyber strategy is espionage; 71.5% of cyberattacks with a known purpose were likely for information collection.
- North Korea has rarely conducted disruptive or destructive cyberattacks in the last 14 years in relation to the overall amount of cyber activity attributed to actors sponsored by the regime.
- North Korea primarily conducts computer network operations in Asia; 77.4% of the cyberattacks for which we have geographic region information took place in Asia.
- The top 5 industry verticals targeted by North Korean state-sponsored threat actors in
descending order are government, cryptocurrency, media, traditional finance, and defense. - Individual North Korean threat actor groups display differences in the purpose of their
operations, their targets, and the geographic regions where they are most active. - Kimsuky and APT37 primarily target entities in Asia, whereas Lazarus and its subgroups have a
more dispersed targeting profile. - In the near-term, North Korea will most likely continue to consistently conduct cyber-espionage.
and financially motivated cyberattacks to support its strategic goals.
Background
The regime uses a combination of criminal activity, terrorist attacks, and nuclear weapons development to achieve 2 goals: perpetuation of the Kim regime and unification of the Korean peninsula under North Korean leadership.
- North Korea has long recognized the values of science, technology, engineering, and math education and nurturing promising domestic talent. An education program for gifted youth was set up in 1960, followed by the establishment of a similar program at Pyongyang’s Pyongyang Senior Middle School No.1 in 1984. The regime then reportedly sends the programs’ top 100 students in computer science to Kim Il Sung National Defense University for further education. University students who excel are then sent to China and Russia where they are exposed to additional computer science education and access to the outside world. The students also gain exposure to technology not easily available in North Korea due to sanctions, such as servers, routers, and other networking equipment they will be expected to exploit in their future careers.
Methodology and Scope
2 Lazarus sub-groups are separated in this report because the industry tracks them as separate entities. The threat actors we tracked in this report are:
- Lazarus: an umbrella term covering several state-sponsored threat groups that have conducted espionage and financially motivated cyber activities on behalf of North Korea since at least 2009.
- APT38: primarily conducts financially motivated cyber operations and has been active since at least 2014. The group has overlap with campaigns attributed to the Lazarus Group and some researchers classify it as a subgroup of Lazarus.
- Andariel: conducts both destructive and financially motivated cyberattacks against primarily South Korea-based entities and has been active since at least 2009. The group has overlap with campaigns attributed to the Lazarus Group and some researchers classify it as a subgroup of Lazarus.
- Kimsuky: primary focus is cyber-espionage operations (with occasionally seen, financially motivated cyberattacks) since at least 2012.
- APT37: gathers information to support North Korea’s national interests, and has been active since at least 2012. The group’s tactics, techniques, and procedures (TTPs), tools, and targets overlap with Kimsuky, likely due to similar missions between North Korean cyber operators.
Threat Analysis Figures
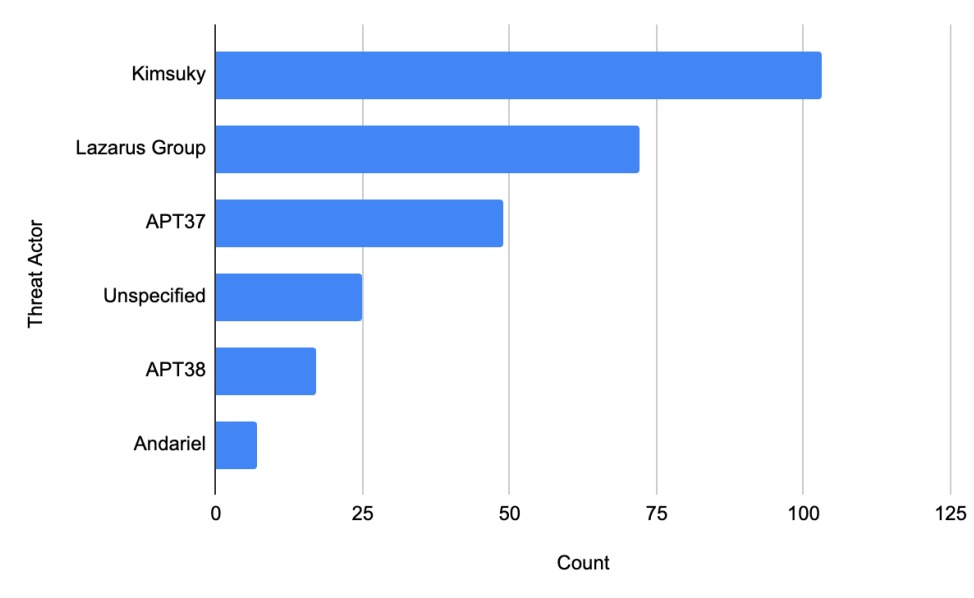
Number of appearances of each North Korean state-sponsored threat actor in the data set
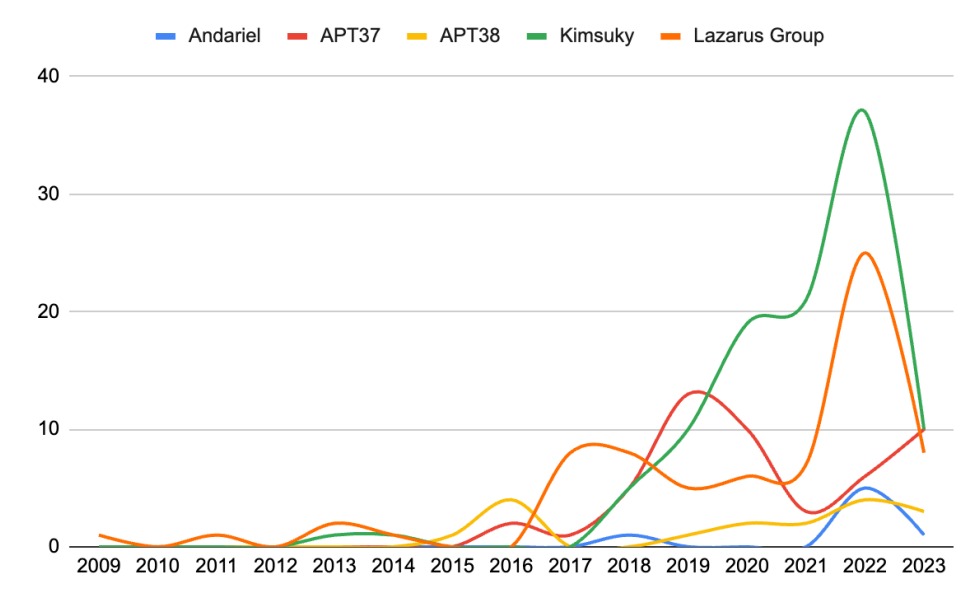
Timeline of cyberattacks broken down by threat actor group. Note: Attacks for 2023 only go to May and, based on
current projects, will likely be much higher than years prior to 2022.
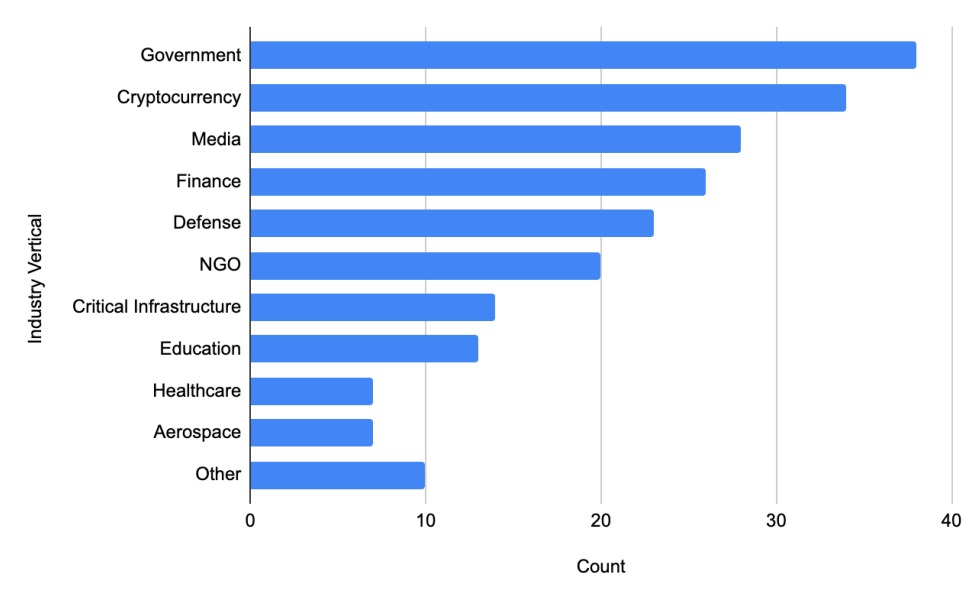
Breakdown of industry verticals of victims targeted by North Korean state-sponsored threat actors
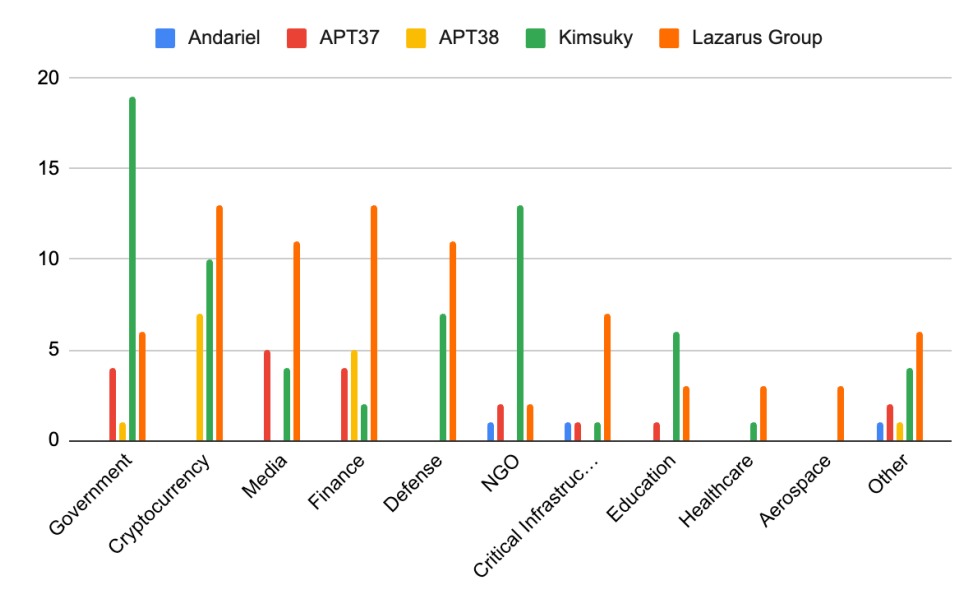
Breakdown of industry verticals of victims grouped by North Korean state-sponsored threat actors
- Kimsuky heavily focuses on government and NGO targets
- Lazarus Group has a diverse target set, but focuses slightly more on cryptocurrency and traditional finance
- APT38 conducts almost solely financially motivated cyberattacks
- Similar to Kimsuky, APT37 targets more government and media entities
- Andariel had the least amount of cyberattacks with known industries of the victims; its attacks were for information collection operations
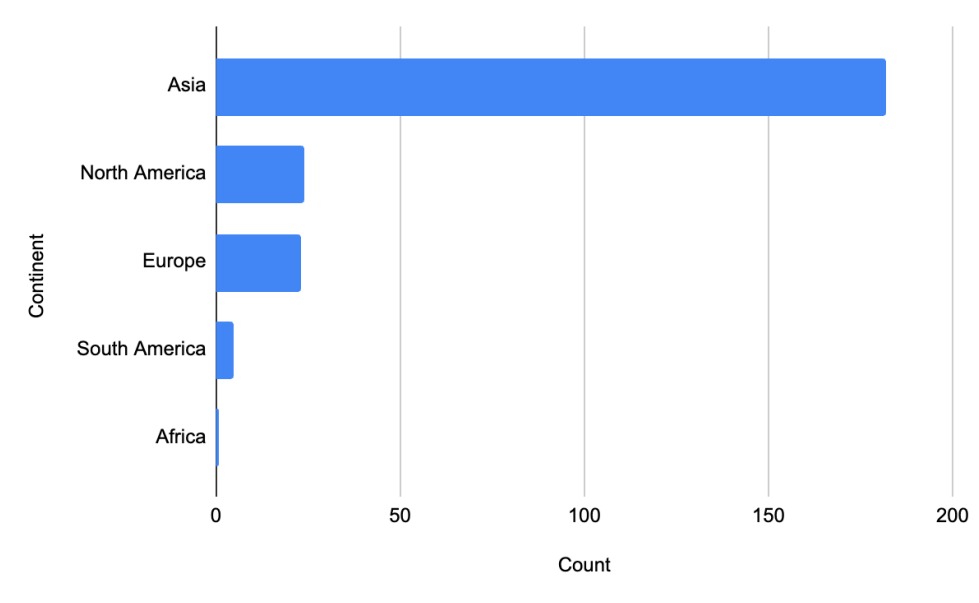
Geographic region of targeted victims in the data set
While several high-profile cyberattacks in North America and Europe have made headlines in the past, such as the Sony Pictures wiper incident in the US and WannaCry ransomware affecting the United Kingdom’s (UK) National Health Service (NHS), the data shows that the overwhelming majority of North Korean state-sponsored activity remains targeted against entities in Asia.
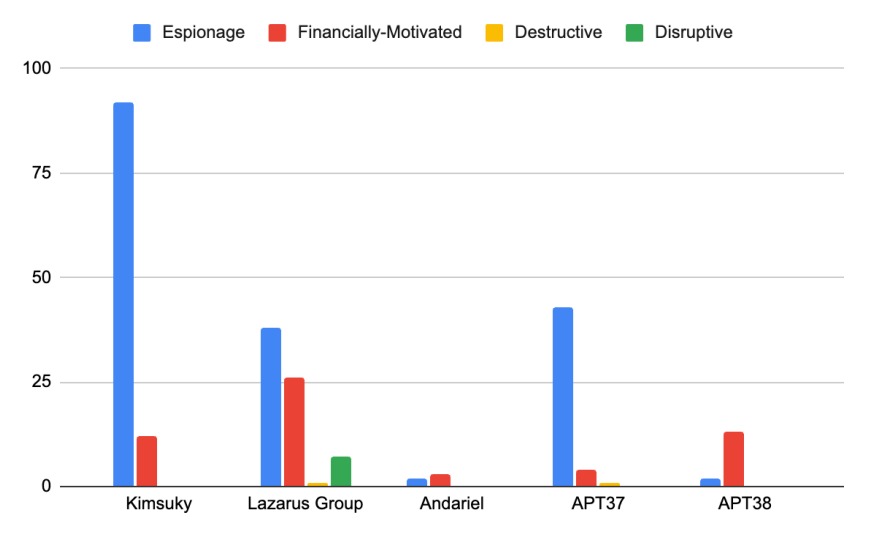
: Breakdown of the purpose of cyberattacks by threat actor group
Taking all of the above into account, we can see that despite the widespread media coverage linked to North Korea’s theft of cryptocurrency or other financial assets and involvement in destructive attacks, the regime is primarily engaged in cyber espionage, with financially motivated activity an increasingly important but secondary goal. Disruptive and destructive cyberattacks are rarely seen in the data.
North Korea’s leadership appears to be much more interested in learning about what others think of them, gathering information that can help them develop nuclear and ballistic missile technology, and stealing money to fund their regime.
Outlook
The two primary objectives, espionage and financial theft, support the regime’s broader goals of securing the leadership position of the Kim family and collecting information against its longtime adversary, South Korea, in order to better anticipate the operational environment during heightened tensions or conflict.
In both the short and long run, Insikt Group expects the regime to continue to consistently conduct cyber-espionage and financially motivated cyberattacks to support its strategic goals, especially as the regime remains under international sanctions.




such a dystopian image, that kim jong un brought into life. and no one is standing against their unreal and unbelievable governing policies